The cyber security threat landscape has gotten a lot worse since the start of the COVID-19 pandemic. Businesses and entrepreneurs are at more risk than ever before; in fact, according to the AV-Test Institute of IT Security, Germany, there were 137.7 million new malware samples in 2020. As of August 2021, 117 million new malware samples have already been found.
However, a not-so-new malware is on the rise again and targeting Windows PCs. It’s called the LemonDuck malware, and while it may sound cute, it's equipped to steal your data and do damage to your systems. So let’s explore its dangers and how you, or your business, can stay protected.
What Is the LemonDuck Malware?
LemonDuck is an actively updated and robust malware that has been on the cybersecurity radar since May 2019. It first gained infamy for botnet and cryptocurrency mining attacks, and since then, it has evolved into a highly sophisticated malware.
LemonDuck is a cross-platform threat that targets both your Windows and Linux devices. It employs a variety of different attack vectors to spread itself, such as phishing emails, exploits, USB devices, and brute force, among others. Microsoft has warned that, beyond using resources for its traditional bot and mining activities, LemonDuck can now steal your credentials and remove security controls from your systems.
It doesn’t care for domain boundaries and moves laterally across your applications, endpoints, user identities, and data domains. It can install tools for future human-operated attacks, and defending your systems can be challenging if you don't know what you're doing.
Why You Should Take the LemonDuck Threat Seriously
In its early days, LemonDuck targeted mostly China and didn't go much further than that. Today, its operations have expanded to several countries: the United States, Russia, China, Germany, the United Kingdom, India, Korea, Canada, France, and Vietnam have all suffered the worst in recent times.
LemonDuck infects systems by disguising itself as harmless files we see on an everyday basis. It's easy to fall prey to it, as it uses current news, events, or the release of new exploits to run effective campaigns and lure its targets.
For example, Microsoft's post discussing the malware states that it spotted LemonDuck using COVID-19-themed lures in email attacks back in 2020. In 2021, it exploited newly patched Exchange Server vulnerabilities to gain access to outdated systems.
Moreover, LemonDuck doesn't stop at exploiting new or popular vulnerabilities. If your organization has old unpatched vulnerabilities in its system, LemonDuck can exploit those while you focus on patching a new vulnerability instead of fixing what's already known.
What makes LemonDuck even more dangerous is that it does not tolerate any other attackers around it. In fact, LemonDuck removes them from a compromised device by getting rid of competing malware. It also prevents any new infections by patching the same vulnerabilities it used to gain access.
Keep an Eye Out for LemonDuck's Evil Twin, LemonCat
The Microsoft 365 Defender Threat Intelligence Team has also exposed the LemonCat infrastructure in its report. LemonCat also uses LemonDuck malware, but a different organization operates it for its own goals.
It uses two domains with the word “cat” in its domains (sqlnetcat[.]com, netcatkit[.]com) and was seen exploiting vulnerabilities in Microsoft Exchange Server when it emerged in January 2021.
You should be wary of LemonCat as it is used for dangerous operations that compromise your data and systems. Today, hackers use LemonCat to install backdoors, credential and data theft, and malware delivery of payloads like the Windows Trojan "Ramnit."
But just because LemonCat is used for more dangerous assaults does not mean you should take LemonDuck malware less seriously. In fact, these findings bring to light how dangerous this dual-threat can be to Windows devices. Attackers can re-use the same set of tools, access, and methods at dynamic intervals to cause greater harm to your enterprise than anticipated earlier.
How You Can Stay Protected With Microsoft 365 Defender
Hopefully, you already have a system in place that can protect you from cyber security threats. For example, you may already have effective antivirus software and installed security tools on your systems. If not, you should consider getting Microsoft 365 Defender if you want protection on an enterprise level.
Microsoft 365 Defender is a unified enterprise defense suite that comprises the Microsoft Defender for Endpoint, Microsoft Defender for Office 365, Microsoft Defender for Identity, and Microsoft Cloud App Security solutions.
Microsoft 365 Defender can help you detect security risks, investigate attacks on your organization, and automatically prevent harmful activities. This integrated cross-domain threat detection and response solution provides your organization with coordinated and automatic defense to block threats before they become attacks.
Its AI-powered industry-leading protections can help you to overcome the wide and sophisticated threats of LemonDuck. A good example is Microsoft 365 Defender for Office 365, which detects the malicious emails sent by the LemonDuck botnet to deliver damage-causing malware payloads.
On the other hand, Microsoft Defender for Endpoint detects and blocks LemonDuck implants, payloads, and malicious activity on Linux and Windows devices.
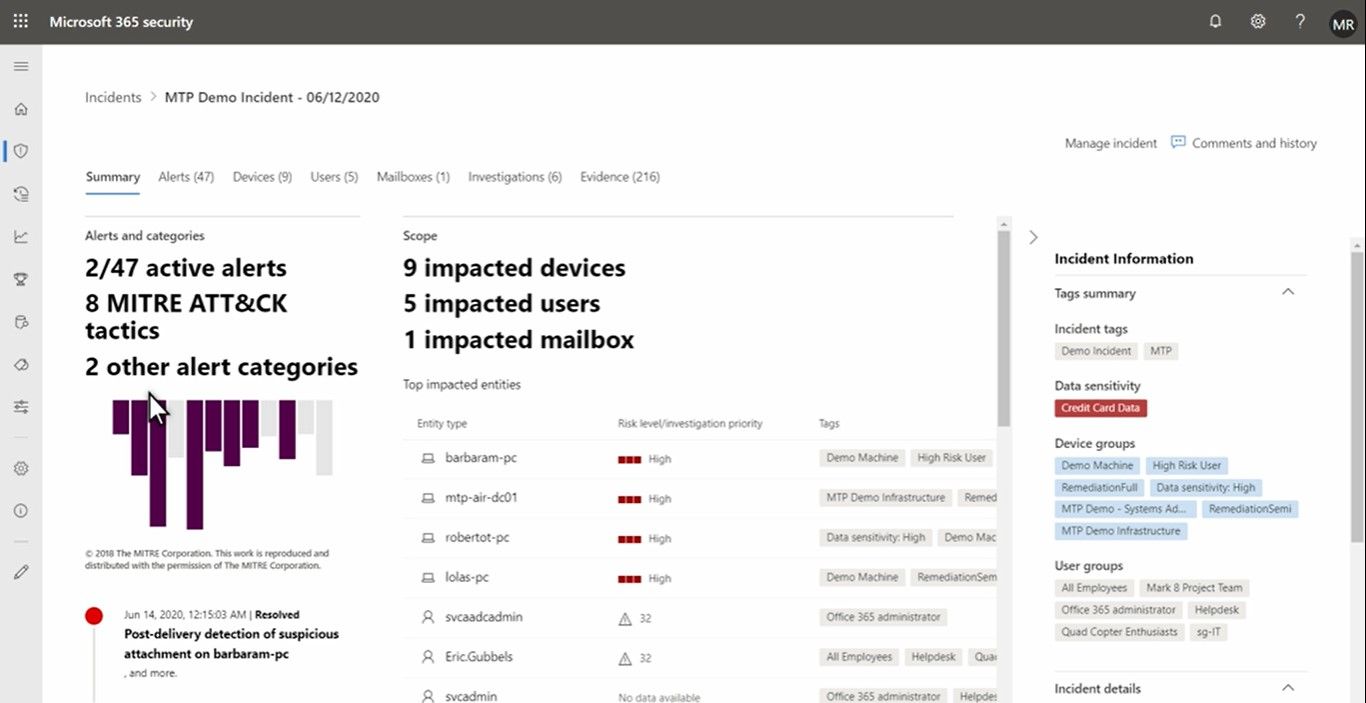
With Microsoft 365 Defender, you have rich investigation tools that your security team can use to expose detections of LemonDuck activity. It analyses and normalizes alerts and connected events and fuses them into incidents to give you a complete view and context of an attack-all in a single dashboard.
Moreover, it even exposes attempts to compromise and gain a foothold on the network, so security operations teams can efficiently and confidently respond to and resolve these attacks.
How You Can Deploy Microsoft 365 Defender for Your Enterprise
As described in the official Microsoft 365 Defender documentation, the service automatically turns itself on if an eligible customer with the required permissions visits the Microsoft 365 Defender portal.
You can use Microsoft 365 Defender at no additional cost if you have a license to a Microsoft 365 security product like Microsoft 365 E5 or A5, Windows 10 Enterprise E5 or A5, and Office 365 E5 or A5.
What More to Do to Keep LemonDuck at Bay
You can also apply certain mitigations to strengthen your defense and reduce the impact of the LemonDuck malware.
- Regularly scan your USB and removable storage devices and block them on sensitive devices. You should also turn off autorun and enable real-time virus protection.
- Be wary of suspicious emails. LemonDuck has been using email attacks with subjects like “The Truth of COVID-19”, “HALTH ADVISORY:CORONA VIRUS,” “What the fcuk,” “This is your order?” and more. There are three types of attachments used for these lures: .doc, .js, or a .zip containing a . file. Whatever the type, the file is named “readme.” Occasionally, you’ll find all three in the same email.
- Encourage the use of web browsers that support SmartScreen in your organization. SmartScreen identifies and blocks malicious websites, including phishing sites, scam sites, and sites that contain exploits and host malware.
There are other important mitigation recommendations that you can read about in Part 2 of Microsoft’s blog series. There, you will also get to explore an in-depth technical analysis of the malicious actions that follow a LemonDuck infection and get guidance for investigating LemonDuck attacks.
Keep Your Organization Protected
LemonDuck and LemonCat are threats that you should take seriously. Constantly evolving multi-component malware like these can devise new ways to access and harm your Windows devices and your business assets.
However, you can stay protected by staying alert and updated and making smart choices. Such as deploying a robust security tool like Microsoft 365 Defender to enable your security team to detect, analyze, and eliminate threats before they can harm.